Modern software development practice is almost only possible with continuous integration and continuous delivery (CI/CD). Ensuring the safety of this process is key to the success and viability of the entire business. This complex undertaking includes securing the development environment, code repository, build system, deployment pipeline and delivered software.
In our article, we will explain how to do this correctly and which specialist should handle this issue, outlining the areas of responsibility of DevOps, DevSec, and SRE.
What is the role of CI/CD in the development cycle?
First, remember a clear definition of CI/CD (Continuous Integration/Continuous Deployment). It is a practice aimed at improving and automating the processes of software development, testing, and deployment. CI is responsible for the frequency of code integration by developers into the main branch of the repository. Moreover, every change made is automatically tested, which allows you to quickly detect and eliminate errors. CD, in turn, is the process of automatically deploying already tested code to the production environment. If all tests pass, the new code is automatically sent to users.
This process not only improves the efficiency of the development process but also provides several other advantages:
- Risk reduction: all errors are detected and resolved quickly, eliminating the threat of critical problems in the future at the sales stage.
- Acceleration of release: the user receives ready-made updates faster and more stable product operation in case of failures.
- Improving the final product quality: automated tests ensure stability and high quality of the code.
So, how does CI/CD work in the development cycle?
A short explanation can be found in this diagram:
- The developer writes code and commits to the repository.
- After this, the CI system runs tests to check the existing changes.
- If the tests are successful, then the CI system builds the application.
- The CD system then automatically deploys the new version of the application to the server.
This is where real-time application monitoring also comes in handy, allowing problems to be quickly identified and resolved.
The tools for implementing CI/CD today are quite impressive and depend on the professionalism and/or preferences of the specialist. But it can be roughly divided into categories according to stages:
- CI tools: Jenkins, Travis CI, CircleCI
- CD tools: Docker, Kubernetes, Spinnaker
- Version control systems: Git, GitHub, GitLab
Examples Of Using CI/CD
Depending on the type of work expected, CI/CD may have a different implementation format. Understanding these aspects is important in order to attract specialists with the necessary skills and experience to the project. Let’s look at some examples.
- Web applications:
- CI: GitHub Actions are used to automatically test each commit in the repository.
- CD: Deploy the web app to Heroku if the tests are successful.
- Mobile applications:
- CI: Use Travis CI to run automated tests and build Android APKs.
- CD: Deploying built versions to platforms such as Firebase App Distribution for internal testing and early access.
- Microservices:
- CI: Jenkins for automatic testing and building Docker images for each microservice.
- CD: Kubernetes automatically deploys and scales microservices in cloud infrastructure (for example, Google Cloud).
- E-commerce:
- CI: CircleCI is used to test code changes and check website functionality.
- CD: AWS CodeDeploy for automatically deploying new site versions on Amazon Web Services servers.
- Web applications:
When To Use Certain Implementations
- GitHub Actions: This is suitable for all projects hosted on GitHub and has simple CI/CD processes.
- Jenkins: optimal for complex and large projects that require flexibility and the ability to integrate with various tools.
- Docker and Kubernetes are suitable for projects with a microservice architecture that requires constant scaling and isolated environments.
- Heroku and AWS CodeDeploy: Suitable for quickly setting up and deploying applications with minimal effort, especially for startups and small businesses.
Thus, each individual case has its specifications and budgets for implementation, so it is necessary to take them into account when choosing and further using it.
Common CI/CD Security Components And Issues
Since the CI/CD process has several components, a security issue can arise at any stage. And the specialist’s task is to ensure high-security measures.
CI/CD security components include:
- Static Application Security Testing (SAST): Scanning source code for known vulnerabilities early in development.
- Dynamic Application Security Testing (DAST): takes place at the end of the CI/CD pipeline and checks an already running application for vulnerabilities.
- Software Composition Analysis (SCA): This component checks open-source code for vulnerabilities.
- Secrets management: we are talking about confidential data (API keys, certificates, etc.)7
- Testing the security of containers: It is important to test the configurations of containers and their reactions to various conditions.
- Infrastructure as Code (IaC) security: This involves analyzing different infrastructure scenarios for misconfigurations or potential violations of security policies.
So, what are the dangers of violating the CI/CD security policy?
- Using unsafe code or third-party components – this way, an attacker can gain access to the code and be on your system.
- Unauthorized access to source code repositories or build tools will entail leakage of data access and unnoticed presence in the system for an unlimited time.
- Providing confidential data to external sources: An attacker can obtain any data from your clients and use it for their own purposes.
Timely identification and mitigation of vulnerabilities throughout the development cycle ensures that code changes are thoroughly tested and meet security standards before deployment to production.
Creating a DevSecOps culture within your development process is the smartest decision you can make. DevSecOps (Development, Security, and Operations) is an approach to culture, automation, and platform design that integrates security as a shared responsibility throughout the IT lifecycle. It is this specialist who is responsible for implementing a secure CI/CD pipeline.
The practice of DevSecOps has much in common with DevOps, but the approach is more global since it is responsible for the entire system. Constant monitoring and feedback regarding potential vulnerabilities act as an alarm for any possible and/or potential problems.
The concept of “shift left” is a fundamental principle in CI/CD and DevSecOps. It refers to moving certain security-focused tasks and activities earlier in the software development process.
There are several steps you should take to protect your CI/CD pipeline. Let’s look at them in more detail:
- Planning: Start by developing a product roadmap with a clear understanding of its stages and potential hazards at each stage. This stage can also be called threat modeling, in which countermeasures should be developed for each potential threat.
- Direct coding: Code must be written according to agreed-upon standards and guidelines. Developers should use validators and scanners to detect code fragments vulnerable to security threats.
- Build: It is necessary to double-check the correctness of the launch and operation of autotests that occur after developers transfer the code to the repository from time to time.
- Testing: Special attention should be paid to new functions, and existing functionality should be noticed.
Thus, in CI/CD, dangers and threats can be literally at every turn. It is important to constantly check and monitor the system to eliminate all problems at the initial stage, not when the threat has already caused consequences.
DevOps, DevSe, And SRE’s Role In CI/CD Security Providing
Since several key specialists are allocated at once when working and supporting project infrastructure today, we decided to pay a little attention to this and explain who exactly your project needs for certain purposes. To begin with, the differences between DevOps, DevSecOps, and SRE can be segmented into three main areas: scope, roles, and goals.
Let’s start in order.
DevOps
DevOps aims to increase the speed of software release by automating processes and optimizing collaboration between development and operations teams. Essentially, he organizes CI/CD from A to Z, helping developers be more efficient and focus on their own tasks.
DevSecOps
DevSecOps goes further by adding to the DevOps practice the issue of ensuring the security of all processes from the very beginning of the development process. They immediately begin deployment, constantly monitor and ensure compliance with security requirements, and, if necessary, train developers.
SRE
SRE still focuses more on ensuring a consistent user experience across different products. The work of SRE is based on a quick response to the needs of the client and the creation of automation processes with a focus on this.
Thus, all three approaches pursue similar goals—ensuring reliability, speeding up the software delivery process, and securing user data. However, they use different strategies to achieve these goals.
- DevOps favors automation.
- DevSecOps emphasizes preventative security measures.
- SRE prioritizes optimization, reliability, and scalability.
Each can significantly contribute when implemented correctly into any organization’s workflow, depending on its specific needs.
Compliance as Code (CaC): What is it and Why is it Needed?
We consider it necessary to also explain Compliance as Code (CaC). In short, it is a technique that helps automate and manage compliance with standards and security requirements using program code. CaC development is carried out by DevOps teams, cloud engineers, and security specialists. The main goal of such teams is to integrate compliance and security requirements directly into the development and operation of the infrastructure.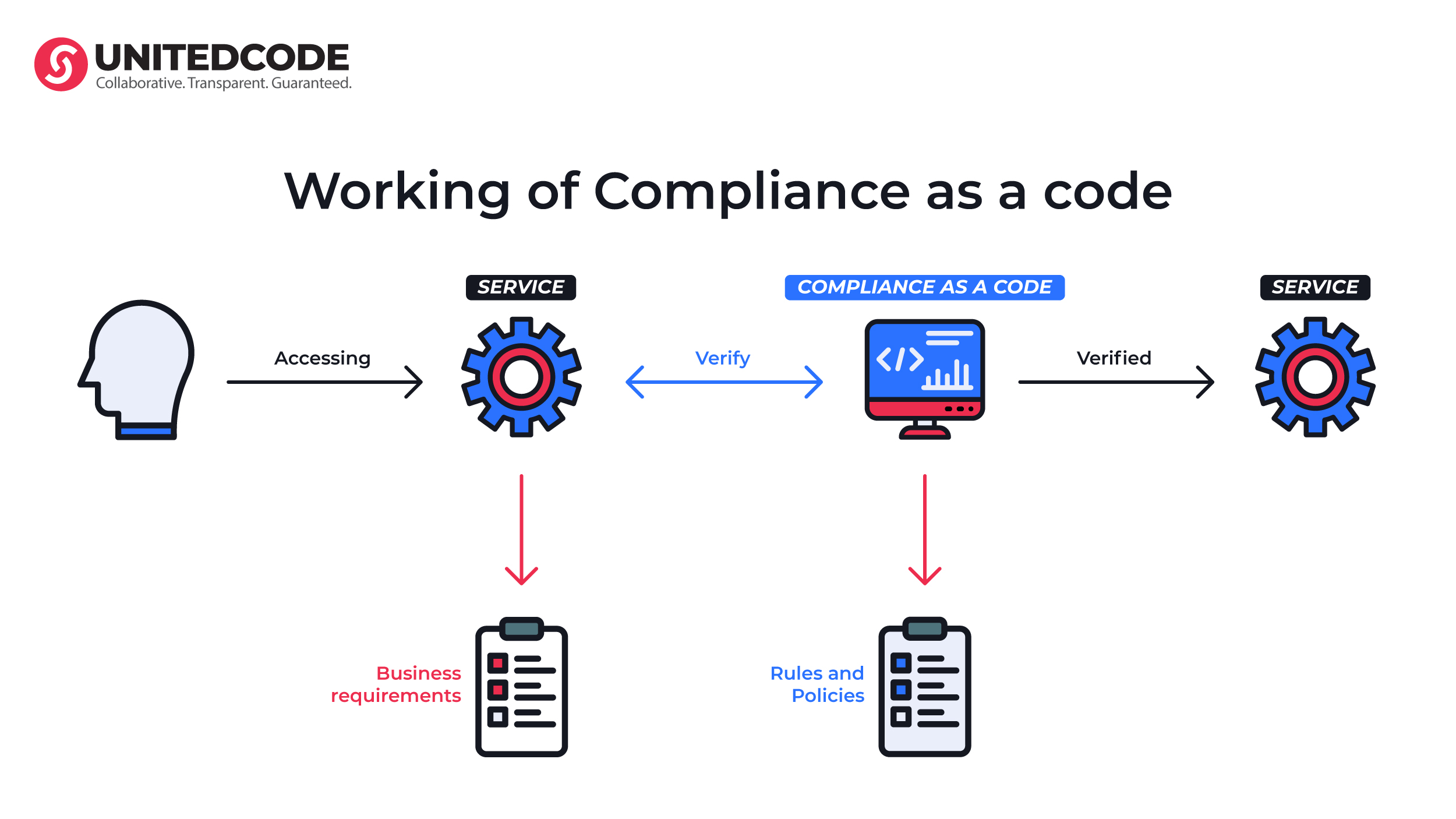
The methodology aims to comply with security measures to protect the code from the beginning of development. It fits well with the concept of ensuring the security of the entire infrastructure in the future, with the transition to automation, minimizing the risk of human errors, and speeding up compliance verification processes. Using CaC increases transparency, improves manageability, and ensures ongoing compliance with security requirements and regulations.
By viewing infrastructure security from a global perspective, you have the opportunity to improve the development process and, more importantly, predict and prevent risks before they arise.
Conclusions
If you want to be efficient and offer users only high-quality solutions without restrictions, you need to use CI/CD, regardless of the size of your business. But you must also understand that, just like at the coding level, you are responsible for the safety and security of your client’s data. Not only the financial component is at stake, but also the reputational one. Before we start selecting an engineer according to our client’s request, we always conduct a thorough analysis of the project and formulate a request for it.
Both DevOps and DevSecOps profiles require CI/CD automation to deliver superior systems quality at greater speed. On the other hand, SRE also seeks to automate the CI/CD pipeline but for a completely different reason: to reduce the cost of failure. By involving an automation specialist (let’s summarize this profile with this name), you relieve the team of the burden of operations such as deployment, application backup, and restarts. All this becomes automated and accelerated.
The trio of DevOps, DevSecOps, and SRE methodologies have the same goal, so they should be viewed as something other than competing positions. Using this expertise, you will notice a significant improvement in the processes within the team responsible for developing and launching your product.
Collaborative. Transparent. Guaranteed. UNITEDCODE
Was this article transparent for you?